
You own your car, and just as with your home, you might assume that what happens in your car stays in your car. It’s your private property, after all.
However, as the era of the connected car is dawning, this isn’t quite true anymore. The average consumer might not realize the risks they’re taking by using a navigation system or plugging their phones into a vehicle’s USB port to charge.
So, here’s a crash course in potential dangers, and how you can reduce risky behavior.
Is Your Car Spying On You?
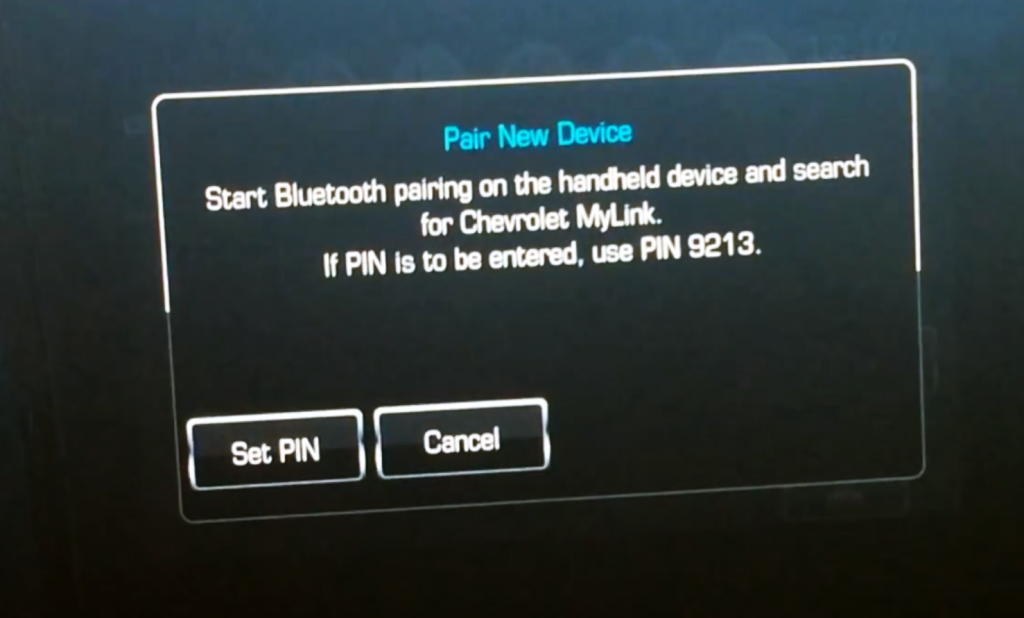
Bluetooth is hackable
Bluetooth wireless technology is common in a broad variety of consumer products; it conveniently connects your smartphone to smart watches, wireless headphones, your computer and, yes, your car.
However, with convenience comes vulnerability.
“The Bluetooth stack is a well-known attack surface,” said Colin Bird-Martinez, a connected-car expert with information-services company IHS Markit. “With access to a Bluetooth connection, hackers could hack the infotainment unit to gain permission to take control over the system, or cause the system to malfunction, or jam the Bluetooth.”
Though this is technically a short-range connection, it is still a potential breach point – both through your car and your phone. You could be giving up contact lists, emails, text messages and photos or – worst case scenario – control of your Bluetooth enabled device without even knowing it.
The good news, however, is that automakers encrypt the data that is shared between phone and car as well as employ multiple security protocols.
“In Audi vehicles, connecting via Bluetooth does not store any personally identifiable information outside of the phone’s display name and removes phone data every time a vehicle is turned off,” said Jacob Brown, senior specialist of innovation and technology communications at Audi USA.
However, even with encryption and protections in place, the first line of defense is always going to be you.
“People typically open the front door and invite the hacker in,” said Robert Kayman, a security consultant with a prominent global technology consulting company. “We are trained to press the button that dismisses the warning dialog as quickly as possible.”
So, before you hit “accept” or “ignore” when pairing your phone or vehicle with a new device, make sure the signal is coming from the actual device you’re trying to connect to.
But to be truly safe, however, experts recommend that turn your Bluetooth off or make it undiscoverable when you’re out in public. Yes, that means disconnecting your Apple Watch or Beats Audio headphones until you get home. If that’s not an option, make sure your device software is always up to date – thus ensuring the most up-to-date security measures.
USB Port: Stranger Danger
When my phone is dying, I rarely think twice about plugging into a USB port in a public space or vehicle. It’s just charging. Right?
Not necessarily. A USB port is designed to transfer data, and if you plug into an infected port, there is a chance you’ve just given a hacker a key to your backdoor. Newer phones have security measures that ask for permissions or may allow you to set your phone to use the USB as a power supply, which helps.
But it’s still no guarantee that your device hasn’t been compromised.
Even if you don’t contract anything malicious from wiring in to an unfamiliar port, you could be leaving something behind – especially in a vehicle.
A blog post on the Federal Trade Commission website points out that when you connect your phone to a car via Bluetooth or USB, the car may keep your phone number, message logs or even your contacts without you even realizing it.
Your best protection: Use a personal USB charger that plugs into the cigarette lighter/12V power outlet.
If you do pair your phone with a vehicle – be it personal or rental – make sure you delete your device and data from the vehicle’s infotainment system before you hand over the keys to another person.
What Your Phone is Telling Your Rental Car
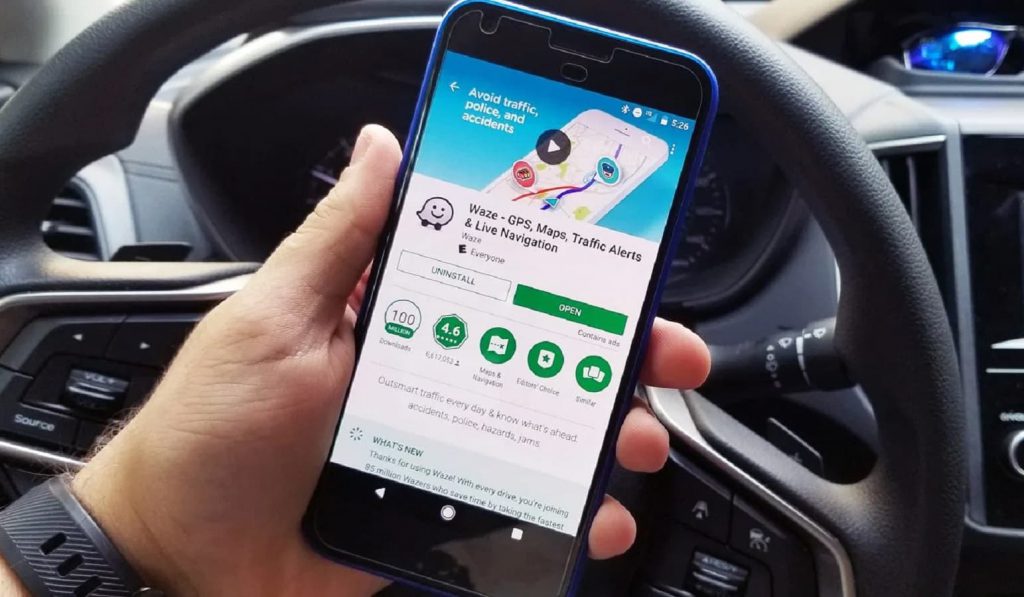
The problem with GPS
A lot of people, myself included, are logistically challenged. They don’t know east from west, and manually reading a paper map seems to have died out with the dodo.
Who needs paper, when you can plug an address into Waze or your car’s navigation system?
While this is certainly convenient, you’re leaving a trail and telling a story every time you input an address. Anyone looking at the data likely knows where you live, work, like to eat dinner, exercise, run your errands, etc.
On the innocent side of things, this data could be used to market products directly to you based on your habits. On the nefarious side, you’ve given someone access to you and your personal safety.
Pair that with an in-car Homelink garage door opener, and Houston, we have a problem. You’re giving away more than access to personal data – you’re giving potential access to your home.
Tech Trouble: Surprising Number Of Drivers Confused By Auto Safety Features
Would you borrow someone’s underwear?
A recent article from Forbes likens the practice of using an unknown charging cable to borrowing someone else’s underwear. If you forgot your underwear on a business trip, you wouldn’t ask to borrow anyone else’s.
Nope. You’d go buy new underwear.
Just like you don’t know where someone else’s underwear has been, you don’t know where common tech items in vehicles have been either.
Some of the safeguards can be simple – like using a personal charging port and turning off Bluetooth functionality in your phone and car.
But the best line of defense is always going to be to knowing where the technology you’re using has been, and abstaining from using it if it’s unknown or unfamiliar. Don’t use the technology just because it’s there.
As Kayman points out: “One infected carrier can cause lots of damage.”
Obviously, the risks are lessened when you’re using the technology in your own car versus a rental.
However, Brown adds: “We recommend users delete their Bluetooth handshake if cycling through vehicles.”
At the very least, lock down your privacy settings on your phone and car, and know exactly what data is being collected by the car, how it’s being stored, and where it’s being used.
Yes, that means you might actually have to read the manual.
If you know your rights and risks, and still choose to engage, Kayman gives this last piece of advice to protect your privacy: “Buy insurance in the form of credit and identity monitoring. Both are now offered at reasonable costs and offer protections in the event of damage.”
Why You Should Never Borrow Someone Else’s Charging Cable
The Bottom Line:
As Brown points out: “Consumers should understand how personal information, including data generated by the operation of their cars, is collected and used by the manufacturer.”
While there are “Automotive Consumer Privacy Protection Principles” adopted by 20 participating automakers, at the end of the day, you are your own biggest advocate.
Younger generations might not blink at privacy issues. They grew up in the era of Facebook, Instagram, and Snapchat, where everything is #LetMeTakeASelfie and post it to the world.
Older generations remember the book 1984 by George Orwell, and think the fiction has finally become fact—only with Siri and Alexa watching their every move.
While the world isn’t a completely private place, it hasn’t quite reached the level of Big Brother. Yet.
So, the moral of the story is: Know your privacy settings on everything so you understand exactly what is being shared. And maybe invest in identity monitoring for added protection.
Auto Alliance Connected-Car Privacy Statement
Is Your Car Spying On You



